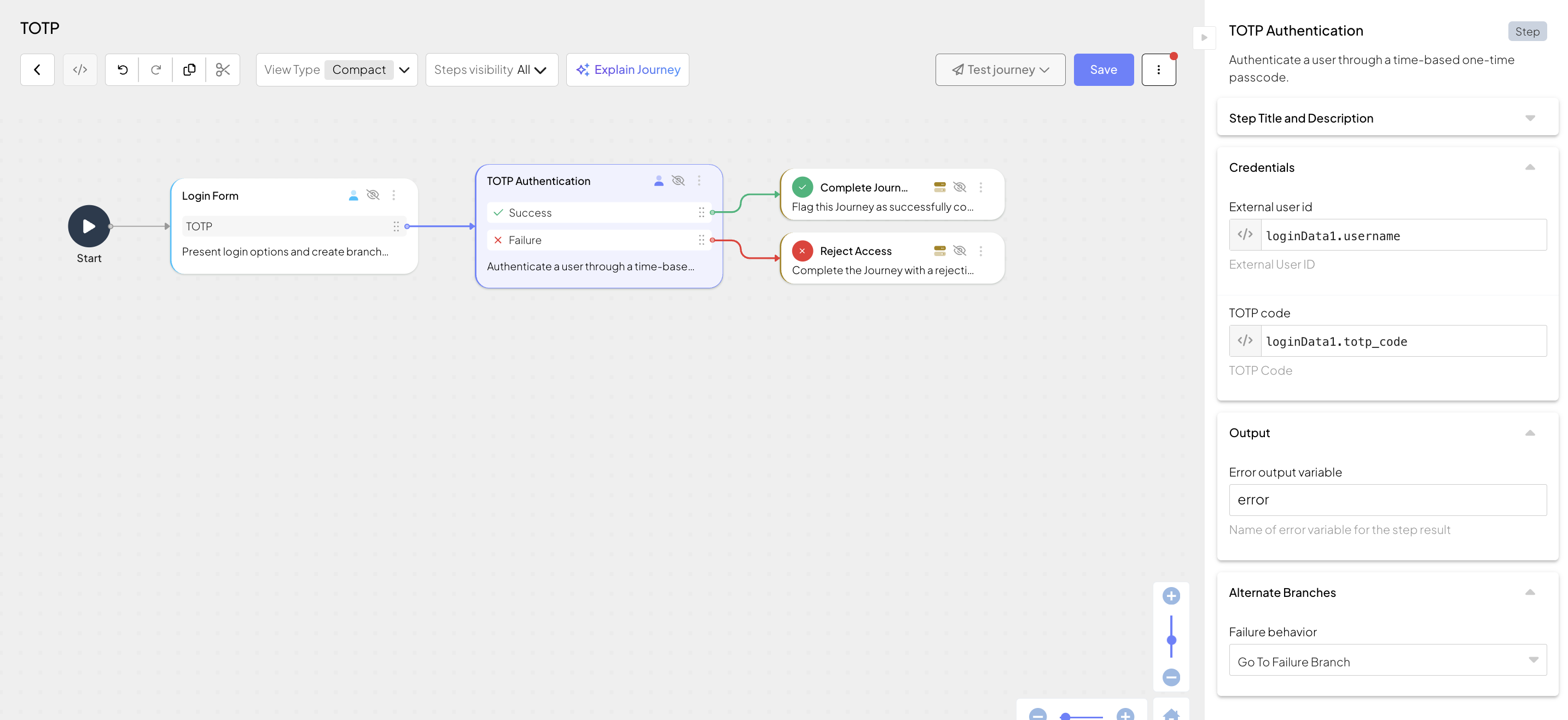
Authenticates the user through a time-based one-time code (TOTP)
This step is used to authenticate the user with a TOTP code they generated using their mobile device. For example, this can be used as a second-factor for MFA, or to step-up authentication for high-risk operations.
To perform TOTP authentication, a user must have a TOTP authenticator registered for the application (via the Register TOTP step). This also involves registering the TOTP secret in a mobile authenticator app (like Google Authenticator), or in another mobile app that implements a TOTP generator.
Before initiating authentication, the journey must obtain the user identifier and generated TOTP code. For example, a form can be used to collect them from the user. When executed, the step validates the generated code against all active TOTP authenticators registered for the user. If successful, the journey sets the user context to the authenticated user and continues to the next step. Tokens generated for the authentication can be accessed in subsequent steps using @policy.userContext().
If it fails (e.g., expired or incorrect code), the journey proceeds to the failure branch (if specified); otherwise, the journey is aborted and an error is sent to the client. When building a TOTP solution, you'll need to consider how to handle the different error cases.
| Field | Description |
|---|---|
| External user ID | User identifier of the authenticating user, specified as an expression. |
| TOTP code | TOTP code to validate, specified as an expression. |
| Org context | Only in B2B journeys. Determines the organization for which the step is executed. By default, the step uses the org context previously set in the journey (e.g., using Select organization step). If set to "manual", you can provide an expression that yields the organization ID. |
| Error output variable | Name of the variable that stores any errors returned by action |
| Failure behavior | Determines the behavior in case of failure, which either aborts the journey or proceeds to a failure branch of the control flow (default). |
Suppose a login form is used to collect the user's username and a TOTP code that they'll generate using their mobile authenticator app. In our example, the form ID is loginForm, the input will be stored in a variable named loginData1, and only TOTP is enabled. The TOTP branch has the default branch ID (totp) and schema (username and totp_code).
The authentication step obtains the username and TOTP code from the form output (loginData1.username and loginData1.totp_code). Once the code is validated, the step is complete.