Monitor your API ecosystem and detect threats in real time with Mosaic’s API Security in the Admin Portal. Designed for fraud and security teams, it provides tools to investigate suspicious behavior, protect sensitive data, and apply risk-based access decisions.
Why API Security matters:
- API discovery and inventory: detect all APIs in your environment, including inactive or misconfigured ones.
- Sensitive data monitoring: identify when requests expose PII or payment data to support compliance.
- Risk-based enforcement: apply access controls or trigger mitigations based on real-time risk signals.
- Visual dashboards: explore API activity, risk trends, and potential abuse through interactive dashboards.
API Security is available via the Admin Portal > API Security.
All API Security data is also accessible via the API Security APIs. You can query risk events (including IPs, ASNs, user agents, risk scores, and challenge reasons), retrieve the API inventory with endpoint metadata, and filter traffic by request type, content type, and geography. This supports integration with custom monitoring tools and automated investigation workflows.
API Security is currently available for customers with Cloudflare or AWS integrations. Additional environments may be supported in future releases.
Mosaic continuously inspects API traffic across your infrastructure by analyzing each incoming request in real time. Each request is enriched with contextual identity signals—such as session token metadata, device or geolocation, and user agent—and passed through multiple detection models to evaluate its risk.
Risk scoring combines identity telemetry, behavioral patterns, and external threat intelligence to flag anomalies such as:
- repeated access to sensitive parameters (e.g., PII fields)
- unexpected traffic from risky ASNs or countries
- staged or spoofed device signals
- request bursts targeting misconfigured or deprecated endpoints
The system continuously learns from historical risk data and model feedback to adapt to new threat patterns over time.
The API Security section provides two dashboards designed for different stages of investigation: one for monitoring and triage, the other for deeper exploration.
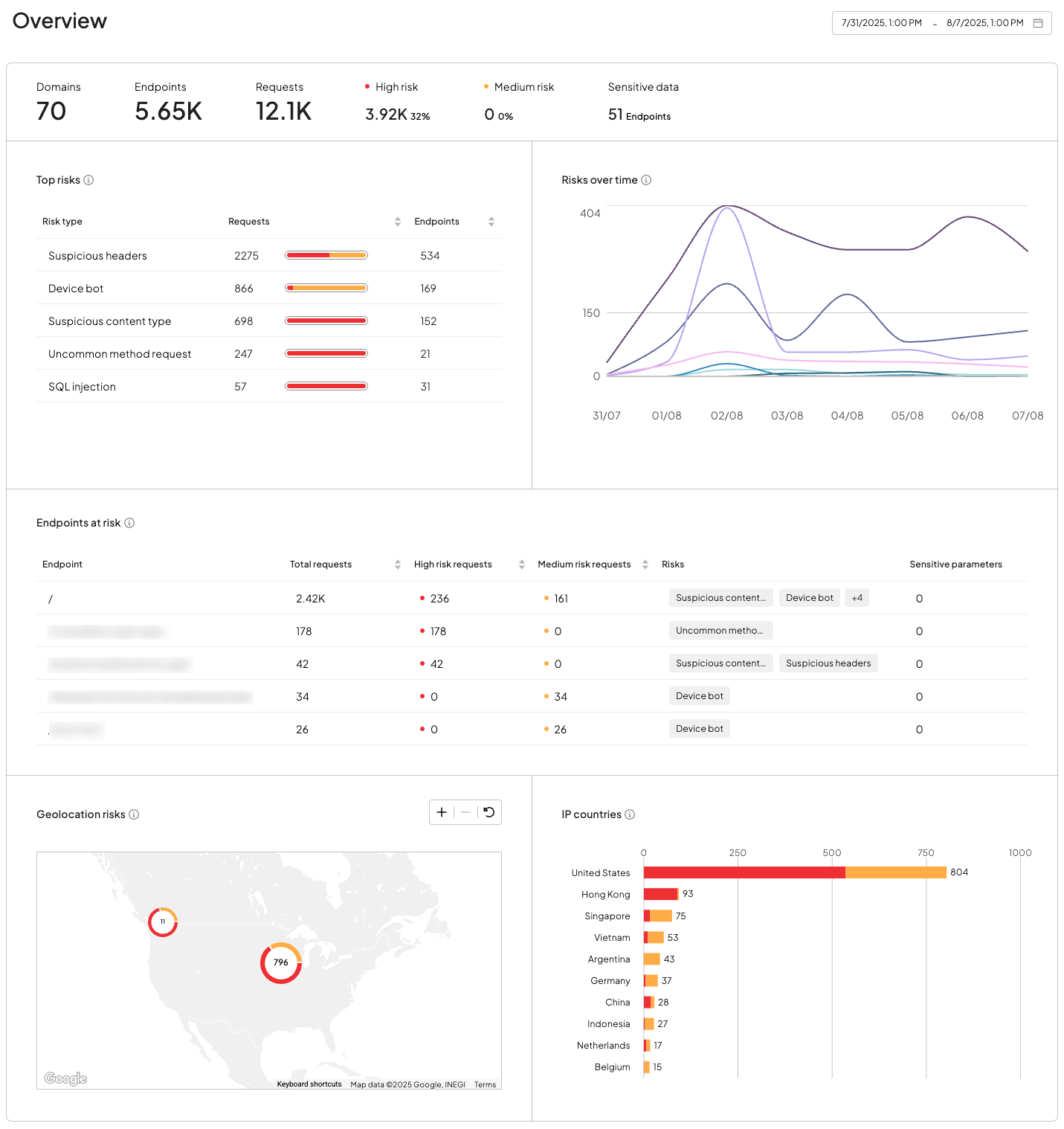
The Overview dashboard provides a live summary of your API risk posture. It surfaces real-time indicators—such as high-risk traffic volume, sensitive data exposure, and top threat patterns—so teams can identify patterns and risk concentration across their API surface.
Use this dashboard to:
- Spot traffic spikes or elevated risk indicators (Top risks, Risks over time)
- Identify which domains or endpoints are being targeted (Endpoints at risk, Top bar metrics)
- See where requests are coming from geographically (Geolocation risks, IP countries)
- Understand why challenges were triggered (e.g., suspicious geolocation, staged devices) (Challenge reasons)
- Detect if sensitive data (like PII or payment fields) is exposed in requests (Sensitive data in top bar)
This view is ideal for real-time monitoring and incident triage, offering a high-level map of your API exposure and how it's evolving.
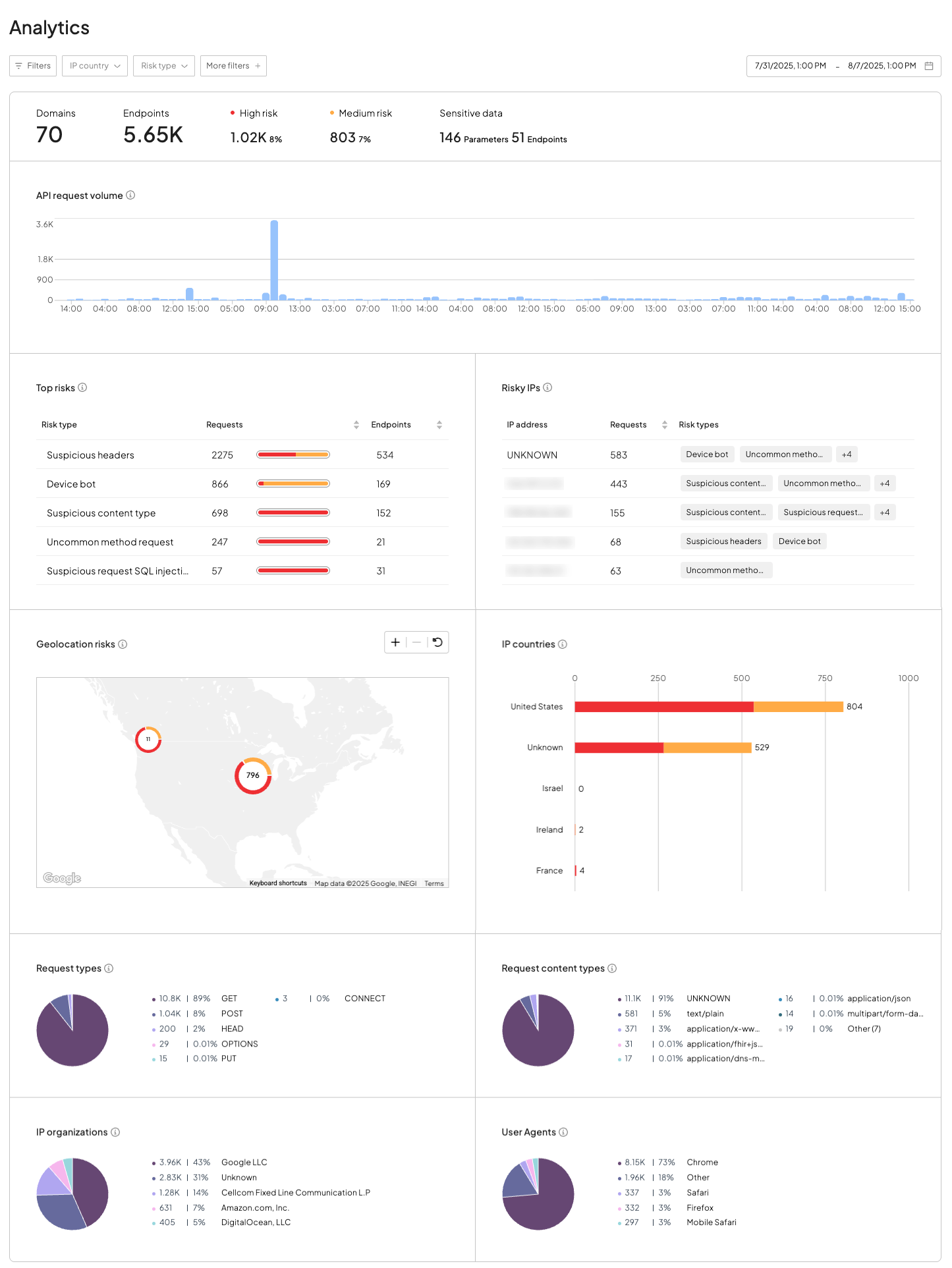
The Analytics dashboard enables detailed, filterable analysis of API request traffic and associated threats. It lets you slice data by request type, content type, IP country, ASN, user agent, and more—revealing how different signals correlate with risk.
Use this dashboard to:
- Investigate top risks across specific geographies, organizations, or traffic types (Top risks, Risky IPs, Geolocation risks, IP countries, IP organizations)
- Trace malicious activity to individual IPs, ASNs, or tools (e.g., via user agent) (User agents, Request types, Request content types)
- Identify which API parameters carry sensitive data most often (Sensitive data in top bar, Parameters)
- Analyze request behavior over time and across multiple dimensions (API request volume)
This view is designed for in-depth investigations, threat hunting, and long-term trend analysis—giving fraud and security teams the flexibility to uncover hidden patterns and respond accordingly.