Mosaic SSO journeys stand apart from regular journeys by combining the seamless authentication experience of OIDC with the flexibility of Journeys, eliminating the need for client-side development. This allows you to focus on creating a login flow tailored to your needs, with SSO capabilities natively built into the SSO journey type. Based on your login needs, SSO can be used to share credentials between RPs, relieving users from the effort of managing multiple credentials.
An SSO journey is created by selecting the SSO-Journey type during journey creation (B2C or B2B Identity based on your setup > Journeys) and using SSO journey steps.
Once the journey is created and saved, you can use it by associating it with a clients group, that are the relying parties that share the same SSO login. The same journey can be linked to multiple groups.
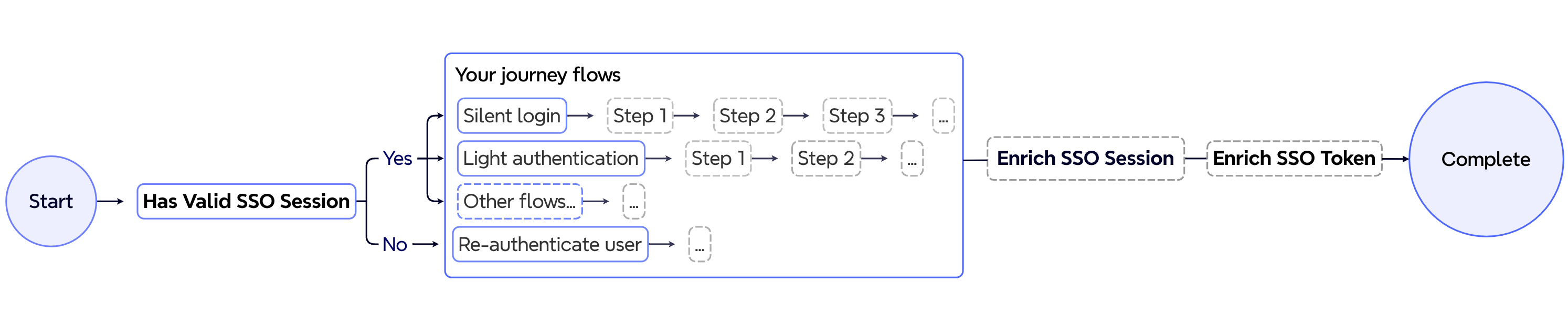
The specific steps included in the SSO journey vary depending on the login flow and the type of SSO experience you want to create. Regardless of the steps that compose the SSO journey, SSO journeys always apply the following SSO logic. A key behavior to note is whether or not the user has an active session.
In the diagram, the actions marked in bold correspond to steps dedicated to the SSO logic.
| Step | Description |
|---|---|
| Start | The journey initiates, exposing parameters such as oidcParams and ssoGroup. For more about how to obtain the incoming parameters and configuration, see the paragraph below. |
| SSO session validity | Determines whether an active user session exists: - Yes: If a valid user session exists, the sessionData (which may include enrichment data collected by the Enrich SSO Session step in previous executions of this journey within the current session) is exposed, and the flow proceeds to Silent Login or Light authentication flows, that rely on the active user context.- No: If no valid user session exists, the flow continues directly to the Re-authenticate journey, that ensures to obtain an active user context. |
| Journey Steps | Executes the SSO journey as designed. The diagram shows two example flows when an active user session is detected: - Silent login: Displays a redirect message and automatically redirects the user to the requested app.- Light authentication: In MFA login flows, collects only a piece of user information to authenticate the user into the requested app.Also included is an example for when no active user session is found. Optionally, the journey logic may include steps to enrich the SSO token and session: - Enrich SSO Token: Adds additional claims or data to the SSO token. - Enrich SSO Session: Enhances the SSO session with more detailed user information or risk recommendations. |
| Complete | The login journey is complete, signaling the client side to redirect back to the RP. |
When an SSO journey starts, you can optionally obtain the incoming OIDC parameters sent by the relying party, as well as the group configuration. To do so, use the @policy.getInteractionParameters() AuthScript expression.
The response can be stored as a variable and used throughout the journey. In general, it has a structure like the example below. interactionParams will include parameters coming from the OIDC request, and ssoGroup includes parameters configured in the client group configuration.
In B2B scenarios, you can also obtain the org context using the @organizations.current() AuthScript expression.
You can also include custom claims in the claims object of the OIDC request. These claims allow you to pass additional parameters, such as user roles, preferences, or application-specific settings, which can be accessed in the journey through @policy.getInteractionParameters(). Additionally, these claims are added to the resulting tokens (e.g., ID Token or Access Token), making them available for downstream applications or APIs that consume the tokens. See custom claims reference and Mosaic token reference for more details.
{
"interactionParams": {
"interactionId": "V9C0dw5vBi5o2C-brxxb0",
"scope": "openid email",
"resource": "https://transmit@identity@security/default",
"clientId": "pohmx1vuvk182qhsbkdygjbg1t95oqqk",
"eventInfo": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6InI2NTBwZWx3Y25rdjNlbGI4ejdkYiIsInR5cCI6IkxvZ2luRXZlbnRJbmZvIiwiaWF0IjoxNzIwMDg3OTExLCJleHAiOjE3MjAxNzQzMTF9.P6zYrGzpomhE1ElXUa1tBrGpCt3DckrYGuTSTsC6S_I",
"redirectUri": "http://acme-a:3001",
"responseType": "code",
"claims": {
"id_token": {
"roles": ["admin", "editor"],
"loa": "3"
}
},
"ssoGroup": {
"id": "zWEqcqgZCuqki6khmOVYO",
"name": "Test SSO Group",
"description": "IDO SSO Group description",
"journey": "sso-test-1",
"sessionTimeout": 50,
"allowSilentLogin": false
}
},
"type": "transmit_platform_interaction_data"
}By leveraging custom claims, you can pass and handle additional user-specific or context-specific parameters directly in the journey, enhancing flexibility and usability.