To prove the identity of your customers, Mosaic performs various checks that depend on the verification flow your app implements. Once a verification process is completed, the verification result will include a recommendation on how to proceed. For example, the diagram below represents the checks performed during the document verification process.
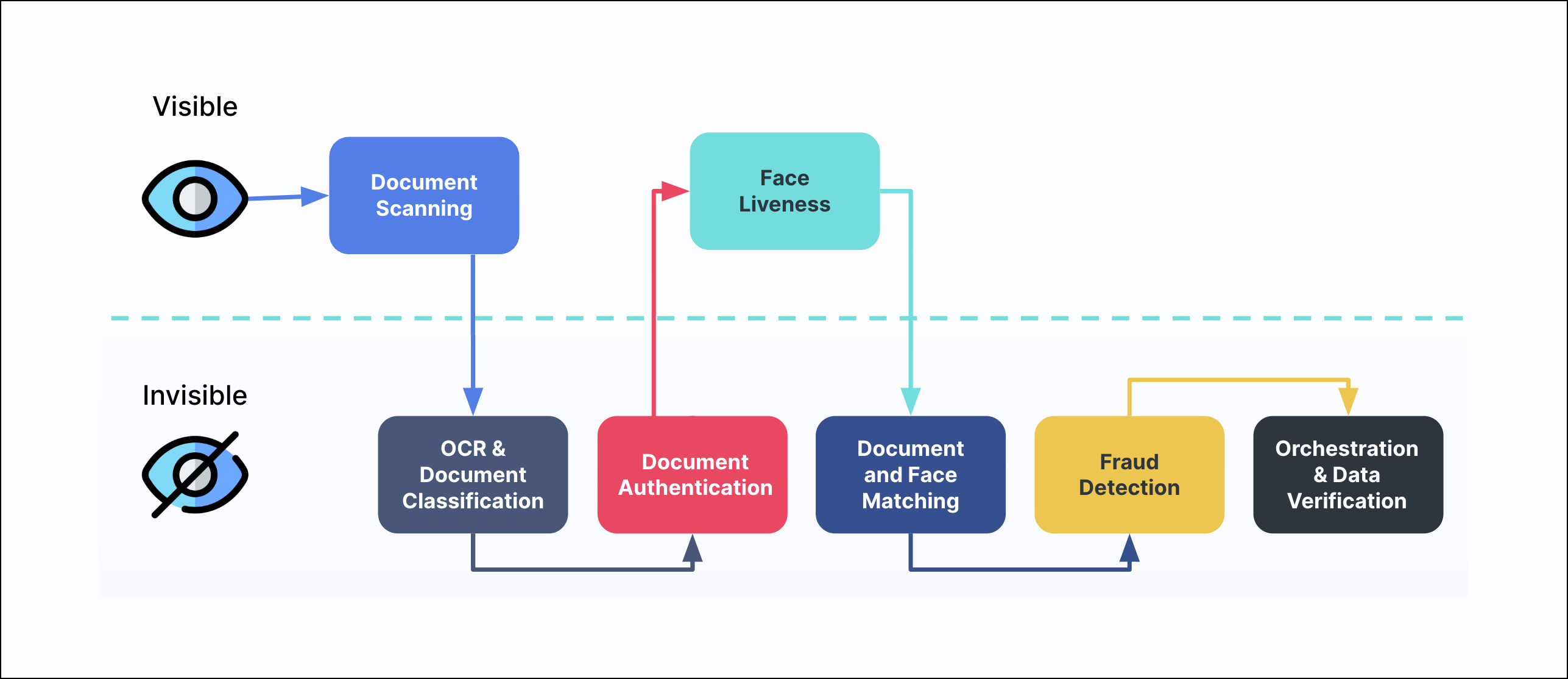
Verifying a government-issued identity document is used to establish the real-world identity of the user. It consists of:
The process begins by scanning a government-issued identity document, such as a driver's license or passport. Using their mobile device, the user takes a picture of the front and back of the document. These images are analyzed in real-time to check for potential issues that may cause them to be rejected and the user is instructed on what to do next. For example, the user is notified if:
- image is blurry
- document isn't supported
- document wasn't captured
- image is too dark
- info is missing or isn't visible
- glare is detected
Once scanned, documents are automatically classified. We support over 10,000 documents worldwide (see Full Global Coverage). If a scanned document wasn't classified, the end user has to resubmit a request.
For example, documents are classified by:
- country
- type (Driver License, Passport, National ID, etc.)
- document template
Mosaic allows you to restrict documents based on specific criteria, such as government-issued IDs, membership cards, or country of origin. Based on your requirements, you can enable several criteria for the same application, allowing for a tailored and efficient document management process. Each criterion comes with a customizable message that is presented to the end user and instructs them on how to proceed with verification, for example, upload additional documents. For more, see Add restriction criteria
The authenticity of the document is validated to make sure it hasn't been altered or forged. This is done by checking:
- security features, such as holograms and laser engravings
- portrait photo issues or inconsistencies
- cross-references of personal and document data throughout the document
- mismatches between the template used and the issue date
- correctly formatted dates (e.g., MM/DD/YYYY vs DD/MM/YYYY)
- correct fonts, including non-generic ones that can't easily be matched
- check digits or checksums in the machine-readable data (MRZ lines)
The document photo is analyzed to validate that it's taken from a physical document. For example, liveness detection is used to detect:
- printed photos
- video replays
- document copies
In face authentication scenarios, a selfie check is used to ensure that the user indeed interacts with the app and is who they claim they are. In the document verification flows, a selfie check acts as a second layer of verification—if the uploaded document proves to be authentic, a check will ensure that it wasn't stolen. The selfie check consists of:
Before a selfie of the user is matched to the photo ID in the document or the reference image, the selfie is analyzed to validate that it's indeed a live person. For example, liveness detection is used to detect:
- printed photos
- video replays
- high-end silicone masks
- photos on screen
- face cutouts
- realistic mannequins
To complete the selfie check, the user's selfie must match the photo ID in the document or the reference image. Our face comparison technology was trained on the massive data set and has been proven reliable, taking into account factors like:
- age-match accuracy
- race
- gender
- black & white vs color photos
To complete this check, Mosaic verifies if the user's selfie biometrically matches any of the flagged identities. The flagged identity check consists of:
Multi-session detection runs automatically during the live verification session to identify anomalies or potential fraud by comparing key data elements (such as face biometrics or profile details) across past sessions. This check helps uncover fraud schemes that rely on reusing biometrics or identity details. For example, synthetic identity fraud—where document data is altered while the same face is reused, or the same personal details are reused across different faces.
Once the documents and selfie are uploaded, Mosaic performs the multi-session detection check by comparing the submitted data against past verifications. If repeated use of the same face or identity details is detected across sessions, the attempt is denied with one of the following reasons:
- Repeated face detected — the same face appears in multiple sessions with mismatched identity details.
- Repeated profile detected — the same identity details (such as full name, date of birth, or gender) appear across different faces.
In the Admin Portal, you can track multi-session detection flags in the Verification overview. In Security insights, you can review and act on these cases, including sessions flagged after the live decision. Although multi-session detection is designed to complete within a strict latency SLA, if the check does not finish in time for the current session, the result is raised as a security insight instead of triggering an immediate deny.
Mosaic automatically checks if the selfie collected during the verification process matches any individual in the face blocklist—a curated gallery of known fraudsters that you've blocked in the past or whose images you've uploaded proactively. Mosaic denies any verification attempts from blocked identities.
Mosaic Fraud Prevention adds an additional layer of fraud prevention to the verification process. In addition to the verification checks, risk and trust are continuously assessed throughout the process. For each user interaction, telemetry data is streamed to the platform. Machine learning models and heuristics are applied to this data to detect risk signals, such as bots, spoofed devices, behavioral anomalies, malicious networks, and more, and issue risk-based recommendations.