How Fraud Prevention works
Fraud Prevention facilitates account protection by allowing you to confidently welcome your credible users, while keeping the bad people out.
Here's how this works.
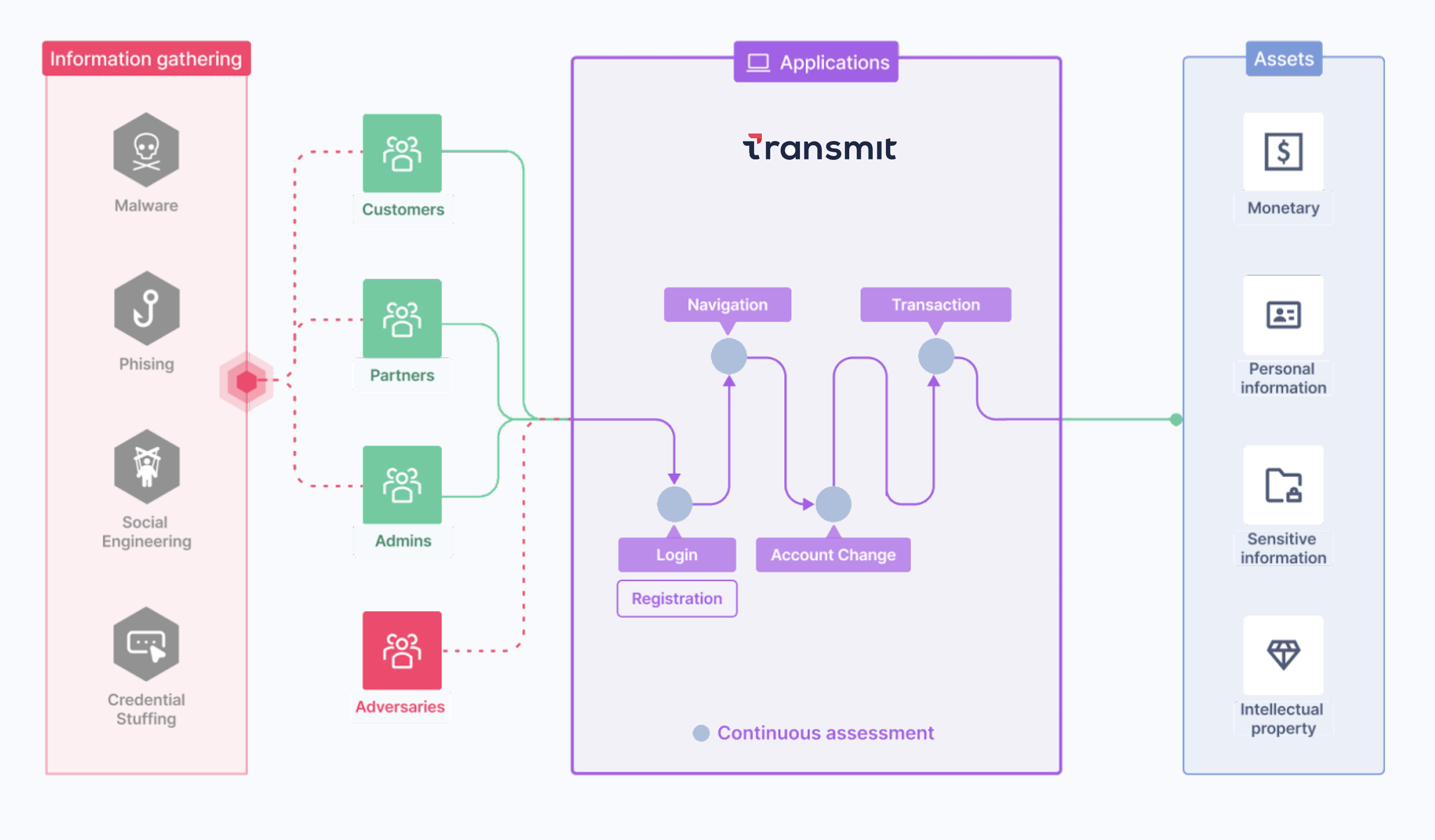
Attack vectors
There are different ways an attacker can engineer an attack. To take over an account, they might start by gathering information so they can disguise themselves as the legitimate user.
Social engineering can be used to influence the victim into immediate action, or to reveal personal details. For example, they could email the user to fill out a form to secure their tax refund, or call to offer free technical support that requires giving over remote access to their computer. Another approach may involve tricking them into installing malware, so they can remotely control the infected device without the user even knowing.
Information gathering may even be as simple as purchasing a list of stolen credentials for a credential-stuffing attack.
Continuous assessment
When ready, the attacker requests access to the app—whether disguised as an existing credible user to take over their account or attempting account abuse as an anonymous user. They may target different actions within the identity journey, such as creating a new account, logging in to an existing one, resetting the account password, making a financial transaction, or checking out a purchase.
When accounts are protected by Mosaic, risk is continuously assessed within the given context (such as user, session, device, action type, etc.) so it can be mitigated effectively. This is done by collecting telemetry data throughout all the user interactions, and analyzing it to reveal any signs of suspicious activity.
This not only reduces account abuse and account takeover, it improves the user experience since users are only challenged when it's actually needed. Friction can even be further reduced for trusted users (e.g., by extending their session). What's more, you can gain insights into the risk and trust of your users in all their journeys throughout the identity lifecycle so you can discover trends and patterns.
Authorized access
Once risk is mitigated or trust is established, the legitimate user can securely gain access to their bank account, their personal data, or any other sensitive assets you'd like to protect.