This guide describes how to quickly integrate Fraud Prevention into your Android application and obtain real-time risk recommendations using Journeys. This guide covers the client-side integration (using the Fraud Prevention SDK and the Orchestration SDK) and the journey configuration needed to complete the flow.
The flow starts with the user navigating to your Android app (1). The Fraud Prevention SDK and the Orchestration SDKs get initialized (2 & 3). The Fraud Prevention SDK starts streaming telemetry data to Mosaic (4). The application requests a device session token (5), the Fraud Prevention sends a request to the Mosaic server (6) and receives a device session token (7), which is then returned to the application (8).
When a user performs a high risk action (9), the application notifies the Orchestration SDK to start a journey (10). The Orchestration SDK invokes a journey (11). Mosaic reaches the risk recommendation step (12) and sends a request to the Fraud Prevention engine (13). As soon as a recommendation is returned (14), IDO processes the risk (15) and passes this data to the Orchestration SDK (16), which then forwards it to the application (17). The application proceeds depending on results (18).
- Android 5+ (API level 21+)
- Allow Mosaic IPs and domains on your network
- Extend the
Content-Security-Policyheader, if CSP is enabled on your web server
Client credentials are used to identify your app and generate access tokens for authorizing Mosaic requests. To obtain them, you'll need to create an application in the Admin Portal (if you don’t have one yet).
- From Applications, click Add application.
- Add the friendly application name to display in the Admin Portal.
- Configure a client: its display name, and your website URL as a redirect URI (e.g.,
https://your-domain.com).
These fields are required for all Mosaic apps, but won’t be used for Fraud Prevention or Journeys.
- Click Add to create your client. This will automatically generate your client credentials.
Journeys can handle the business logic responsible for obtaining risk recommendations for sensitive events. This includes the following configuration steps:
Start by saving the client credentials you've acquired in Step 1 with Mosaic Journeys. This step is required in order to authorize journey calls.
- Navigate to Admin Portal > Journey Tools > Keys and Credentials > Credentials and select +Add credentials.
- Provide an alias and input client ID and secret.
See Key and credentials for more details.
Create a new web function that calls the Trigger action endpoint. See Custom HTTP function for more details.
- Navigate to Admin Portal > Management > Integration hub and Custom HTTP.
- Provide a function name, e.g.,
trigger_action_for_user - Add function argument # 1:
- Argument name:
session_token - Argument description: Fraud Prevention SDK device session token
- Type description: string
- Argument name:
- Add function argument # 2:
- Argument name:
action_type - Argument description: Client provided action type
- Type description: string
- Argument name:
- Add function argument # 3:
- Argument name:
user_id - Argument description: Identifier of an authenticated user
- Type description: string
- Argument name:
- Add function argument # 4:
- Argument name:
correlation_id - Argument description: Interaction ID in your app
- Type description: string
- Argument name:
- Configure the format:
- Request URI:
https://api.transmitsecurity.io/risk/v1/action/trigger-action?get_recommendation=true - HTTP request method:
POST - Request body:
{ "session_token": "${session_token}", "action_type": "${action_type}", "correlation_id": "${correlation_id}", "user_id": "${user_id}" } - Request header:
- Name:
Content-Type - Value:
application/json
- Name:
- Request URI:
- Configure authentication:
- Authentication Type: OAuth 2 Client Credentials Grant
- URL:
https://api.transmitsecurity.com/oidc/token - Credentials alias: select the alias created in Step 2.1
- Scope:
offline_access - Resource:
https://risk.identity.security
- Set the response format to
JSON object. - Save a function.
Configure an identity journey for obtaining risk recommendations and exporting a result.
- In the Admin Portal, go to B2C or B2B Identity (based on your setup) > Journeys and create a new Client SDK journey. Provide a name, e.g.,
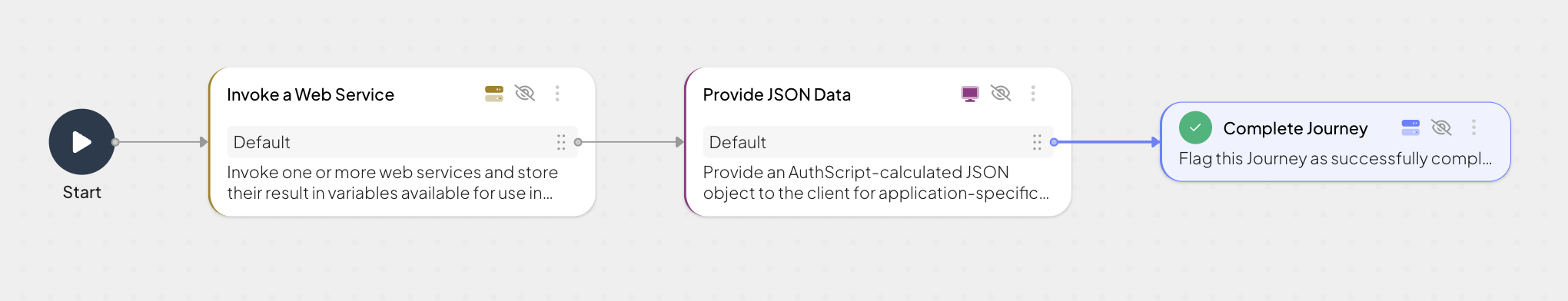
risk-recommendation, and save journey ID. - Add the Invoke Custom HTTP step and configure it to use the web function defined in Step 3.2.
- Configure the step to set its result into the output variable (e.g.,
risk_recommendation). - Configure the step to retrieve the input parameters provided by the client in the journey (see Step 6) as follows:
session_token:@policy.request().params["session_token"]action_type:@policy.request().params["action_type"]user_id:@policy.request().params["user_id"]correlation_id:@policy.request().params["correlation_id"]
- Configure the step to set its result into the output variable (e.g.,
- Add the Provide JSON Data step and set the Data to Send to:
{ "risk_recommendation": risk_recommendation } - Add the Complete Journey step.
Your journey will look as follows:
Add the following lines in the shared build.gradle file ("allprojects" scope):
dependencyResolutionManagement {
repositoriesMode.set(RepositoriesMode.FAIL_ON_PROJECT_REPOS)
repositories {
maven {
url('https://transmit.jfrog.io/artifactory/transmit-security-gradle-release-local/')
}
mavenCentral()
google()
}
}Add the following in the module build.gradle file (project scope):
dependencies {
implementation("com.ts.sdk:accountprotection:2.1.+")
implementation("com.ts.sdk:identityorchestration:1.0.+")
}Initializing the SDKs configures them to work with your client ID. It also allows setting the base URL for the SDK to use, whether a Mosaic-provided path or your own proxy. In case of Fraud Prevention, it starts streaming telemetry data upon SDK initialization.
Initialize using strings.xml configuration (recommended)
To do this, update the strings.xml file in your Application with the following content. The [CLIENT_ID] should be replaced with your client ID from Step 1.
<resources>
<!-- Mosaic Credentials -->
<string name="transmit_security_client_id">"YOUR_CLIENT_ID"</string>
<string name="transmit_security_base_url">https://api.transmitsecurity.io/</string> <!-- Default -->
</resources>The SDK can be configured to work with a different cluster or a proxy by setting transmit_security_base_url to a different URI.
Add the code below to your Application class.
class Application : Application() {
override fun onCreate() {
super.onCreate()
TSAccountProtection.initializeSDK(this)
TSIdo.initializeSDK(this)
}
}Initialize using SDK parameters
Add the code below to your Application Class. The [CLIENT_ID] should be replaced with your client ID from Step 1.
class Application : Application() {
override fun onCreate() {
super.onCreate()
TSAccountProtection.initialize(this, "CLIENT_ID")
TSIdo.initializeSDK(context,
clientId,
TSIdoInitOptions(baseUrl)) // Default is https://api.transmitsecurity.io
}
}The SDK can be configured to work a different cluster or a proxy by setting baseUrl to a different URI.
Obtain a Fraud Prevention device session token by executing the code below. Save the received device session token in order to obtain risk recommendations in the next step (Step 6).
TSAccountProtection.getSessionToken(object : ISessionTokenCallback {
override fun onSessionToken(sessionToken: String) {
}
})To obtain risk recommendations, the journey (created in Step 2) should start in response to sensitive user interactions, such as payments. Your application should present a button and call the below on user click. Along with the journey invocation, pass:
session_tokenreceived in Step 5action_typefrom our list of actions that represents a high risk action the user attempts to performuser_idthat represents a hash of the user logged into the app. The actual user ID should not be sent (this journey assumes the user has already authenticated in your app)correlation_idof the interaction
@Keep
data class Params(val user_id: String, val action_type: String, val session_token: String, val correlation_id: String)
....
// Starts a journey
TSIdo.startJourney([JOURNEY_ID],
TSIdoStartJourneyOptions(Params([USER_ID], [ACTION_TYPE], [SESSION_TOKEN], [CORRELATION_ID]),
[FLOW_ID]), callback)The callback object should implement the TSIdoCallback interface.
Mosaic signals journey completion by setting the journeyStepId property to Rejection.type or Success.type. The Orchestration SDK returns recommendation data (idoServiceResponse.data.json_data) to the application to proceed accordingly.
In your application, add code that performs the appropriate identity protection steps based on the Mosaic risk recommendation. For example, proceed normally if Mosaic returns 'allow', terminate and inform the user of the issue if 'deny', or trigger a step-up authentication process if 'challenge'.