Login with Apple
Overview
Sign in with Apple can be used to authenticate users, or create new users based on their email address.
Here's how it works:
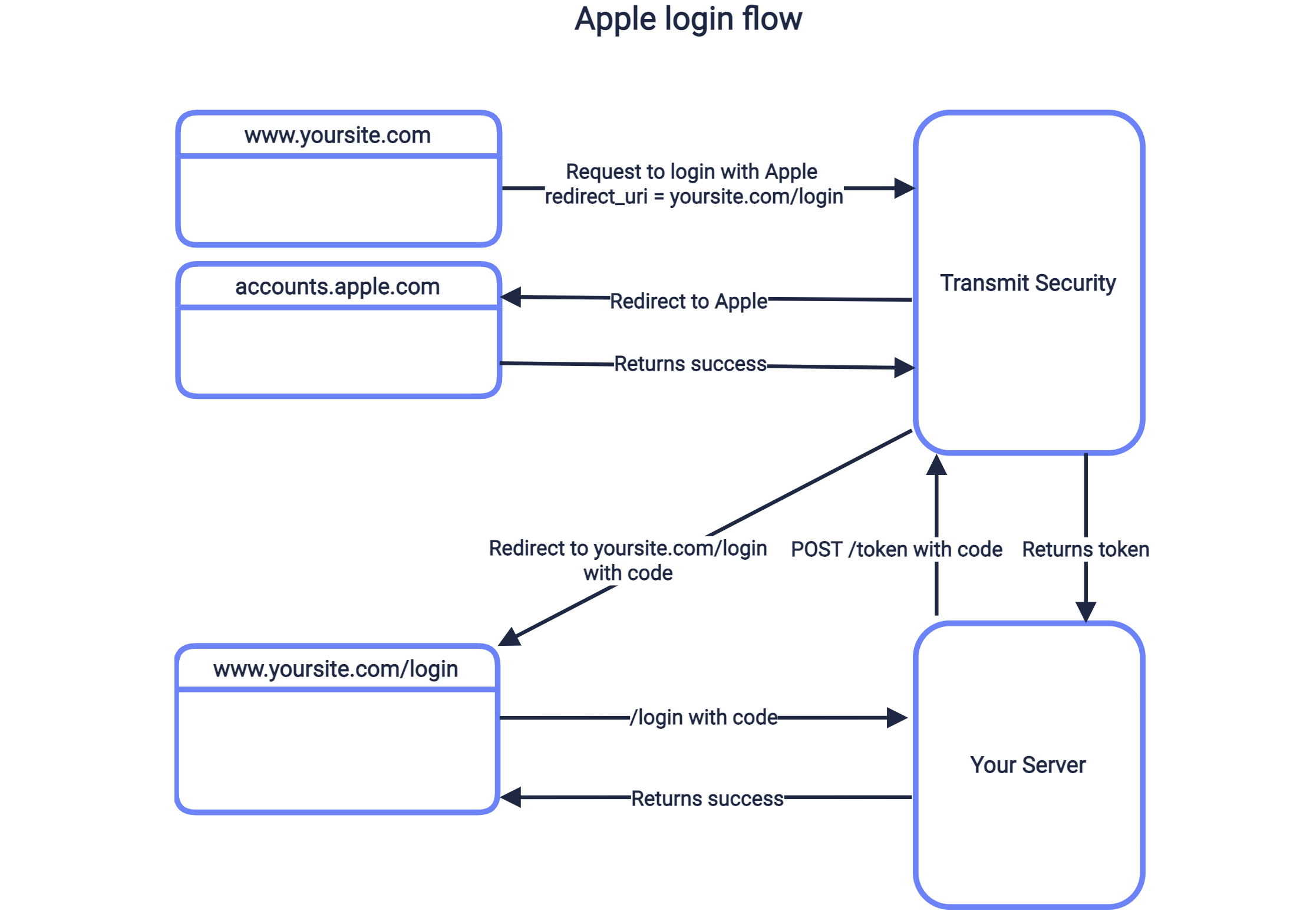
-
User clicks login button, sending request to
/auth/applewithclient_idandredirect_uri - Transmit redirects to Apple login page, which authenticates user and redirects back to Transmit.
-
After validating the response, Transmit redirects back to your
redirect_uriwith a code. - Your application sends the code to your backend, which exchanges it for tokens.
- Upon a successful exchange, the user is logged in.
Step 1: Set up Apple credentials
From the Apple Developer Portal, set up an app using Apple's Sign in with Apple documentation:
-
Create a Services ID and associate with your app via App ID. Add
api.transmitsecurity.io/cisas the Domain and set your Redirect URI tohttps://api.transmitsecurity.io/cis/auth/apple/callback(see Apple docs ). - Generate a Client Secret Signing Key (under Certificates, Identifiers & Profiles ). Obtain its Key ID and download the key itself (see Apple docs ). Transmit will need them to generate an Apple client secret.
- Obtain your Apple Team ID (under Membership Details )
Note
The Services ID, Key ID, Client Secret Signing Key, and Apple Team ID will be configured later in the Transmit Admin Portal.
Step 2: Enable Apple for app
- Login to the Transmit Admin Portal
- Go to Manage Experience > Authentication
- Expand the Apple settings.
- Fill in the client ID (using Services ID), client secret (using Client Secret Signing Key), Key ID and Apple Team ID retrieved from Apple in Step 1.
Step 3: Add redirect URI to app
To redirect back to the redirect_uri provided in the initial request, it should be registered in your application settings in the Transmit Admin Portal. From the Admin Portal under Applications, click on your application to edit your application settings and add this URI under Redirect URIs. If you don't already have an application, you'll need to create one first (see Create application).
Note
Your application settings contain the Client ID and Client Secret for your application, which you'll need for Step 4 and 5.
Step 4: Initiate Apple login
Use a request like the one below to initiate an authentication flow using Apple, described in the sequence diagram above. The create_new_user parameter will determine if this flow applies to new users, or only to existing ones. If set to true (and public sign-ups are enabled for this application), a new user is created if no user is found for the email returned by Apple in the next step. The redirect_uri should correspond to the one added in step 3, and the client_id can be found from the Transmit Admin Portal in the application settings.
Note
Upon successful authentication, the browser will be redirected to the redirect URI along with a code to exchange for tokens in the next step. For example, if https://domain.com/verify is your redirect URI, then Transmit will redirect to https://domain.com/verify?code=123abc. However, if an authentication error occurs after redirecting to Apple, the redirect URI will contain the error instead.
curl --request GET \
--url 'https://api.transmitsecurity.io/cis/v1/auth/apple?
client_id=2eb840f.test.Transmit.io&
redirect_uri=https://www.example.com/login&
create_new_user=true' \
--header 'Accept: application/json'Step 5: Get user tokens
To exchange the code received from Transmit for an ID and access token, your server should send a POST request like the one below to the Transmit /oidc/token endpoint. Replace placeholders with the code you received in Step 4, your redirect URI, and your client credentials that can be found in your application settings from the Transmit Admin Portal.
curl -i -X POST \
https://api.transmitsecurity.io/oidc/token \
-H 'Content-Type: application/x-www-form-urlencoded' \
-d client_id=CLIENT_ID \
-d client_secret=CLIENT_SECRET \
-d code=CODE \
-d grant_type=authorization_code \
-d redirect_uri=REDIRECT_URI